Reset root user password in ESXi 7.x
Sometimes, for one reason or another, you may not be able to authenticate to the ESXi Management Console because you do not have an up-to-date password. This can be due to a system hack, system crash, lost password, or if you inherited ESXi without documentation or proper administrative controls. This is an unpleasant situation and something will have to be done about it. Maybe not immediately, but when something goes wrong and you need to interfere with a system that has been functioning normally up to now. This instruction is written for such cases.
There are several ways to reset the password. However, the one given in this article is universal and will work not only for 7.x versions but also for earlier ones. It has been tested in practice and is working in most cases. So let's get started.
First we need to boot from any Live CD. It can be an Ubuntu installation image or, as in our case, Finnix. This is a debian-based distribution with extensive diagnostic and disaster recovery capabilities.
After booting, you will see a console prompt:
In case your server is located remotely and you are connected to it via IP-KVM, it is not very convenient to work in this mode because of high console response time. To avoid this, you can set up an ssh server. If this is not a problem, you can skip this step.
# set the root password for the live system passwd # bring up the ssh server service ssh star
You can then connect to the server using your favourite ssh client or from the console:
ssh root@1.2.3.4
Now we need to determine which disc contains the partition we need. To do this, let's first determine which discs we have.
root@0:~# lsblk NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTS loop0 7:0 0 377.2M 1 loop /usr/lib/live/mount/rootfs/filesystem.squashfs /run/live/rootfs/filesystem.squashfs sda 8:0 1 3.6T 0 disk └─sda1 8:1 1 3.6T 0 part sdb 8:16 1 3.6T 0 disk └─sdb1 8:17 1 3.6T 0 part sr0 11:0 1 455M 0 rom /run/live/medium zram0 252:0 0 62.8G 0 disk [SWAP] nvme1n1 259:0 0 476.9G 0 disk └─nvme1n1p1 259:2 0 476.9G 0 part nvme0n1 259:1 0 476.9G 0 disk ├─nvme0n1p1 259:3 0 4M 0 part ├─nvme0n1p2 259:4 0 4G 0 part ├─nvme0n1p3 259:5 0 469.6G 0 part ├──nvme0n1p5 259:6 0 250M 0 part ├─nvme0n1p6 259:7 0 250M 0 part ├─nvme0n1p7 259:8 0 110M 0 part ├─nvme0n1p8 259:9 0 286M 0 part └─nvme0n1p9 259:10 0 2.5G 0 part
Our main search criterion is a 250MB disc partition. As we can see, the nvme0n1 disc contains such a partition, let's take a closer look at it:
fdisk -l /dev/nvme0n1
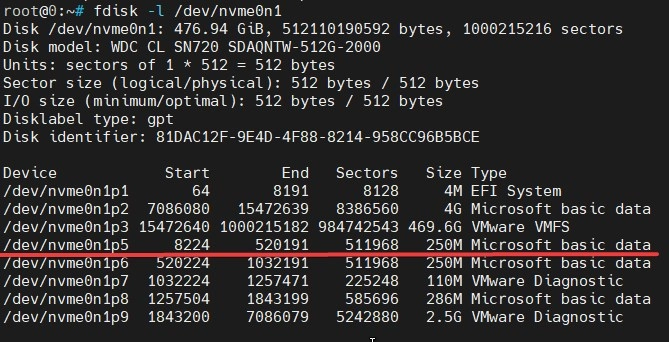
Our target is the partition that starts at sector 8224 and is 250MB in size. This is the partition that contains the data we need
To continue, let's create 2 directories, one for mounting the disc and the other for the data we need to edit.
mkdir /mnt/vmware && mkdir /tmp/vmware
Mount the found partition
mount /dev/nvme0n1p5 /mnt/vmware
There is a lot of stuff inside, but we need a specific file
It should be unpacked into the directory created earlier
tar -xf /mnt/vmware/state.tgz -C /tmp/vmware/ tar -xf /tmp/vmware/local.tgz -C /tmp/vmware/ rm /tmp/vmware/local.tgz
Now if we go to /tmp/vmware/ and look through its contents, we will find the familiar etc directory there.
Next we need to edit the shadow file and remove the root password hash from it. Thus ESXi will think that the user password is empty after our manipulation.
nano /tmp/vmware/etc/shadow
This should be done carefully. It is necessary to delete the content between the first and the second colon
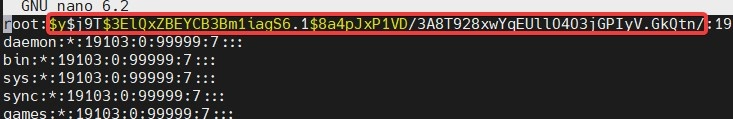
and it should look like this
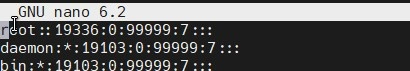
Save the file with the F3 button. This completes the most important part. Next you need to pack everything and put it back where you found it.
cd /tmp/vmware/ tar -czf local.tgz etc tar -czf state.tgz local.tgz mv state.tgz /mnt/vmware/
Unmount the ESXi drive and reboot.
umount /mnt/vmware/ reboot
After reboot, log in to the ESXi web-interface as root user with an empty password and change it to the one we need using standard means via the top right menu.
Potential Issues and Solutions:
- Partition Mounting Error: Ensure that you have specified the correct path to the system disk. Run
lsblkto display the partition structure. - Shadow File Missing: Verify the correctness of the path
/tmp/etc/shadow. Make sure that the archivesstate.tgzandlocal.tgzhave been successfully unpacked. - Password Not Reset: Check that the changes have been saved and the files have been successfully rebuilt and moved to their original location.
That's it! The goal is achieved! We recommend you to save your new password and never lose it again!










































