Configuring Proxmox after installation
There are a few important things to do after installing Proxmox.
Update the system to the latest version
ProxmoxVE by default receives updates from the paid Enterprise repository, updates from which are available to customers with a paid subscription. To get the latest updates without a subscription, you need to disable the paid repository and enable the non-subscription repository. If this is not done, apt will report an error when updating package sources.
1. Log in to the web interface (https://server.ip.address:8006) or connect to the server via SSH.
Let's use the web interface as an example. Go to console:

2. Edit the apt configuration file:
nano /etc/apt/sources.list.d/pve-enterprise.list
There is only one line in this file. Write a "#" symbol in front of it to disable the option of receiving updates from a paid repository:
#deb https://enterprise.proxmox.com stretch pve-enterprise
3. Press Ctrl + X to exit the editor, answering "Y" to the system's question about saving the file.
4. Connect the no-subscription repository. To do this, open the file for editing:
nano /etc/apt/sources.list
5. Add lines to this file:
For ProxmoxVE 7
deb http://download.proxmox.com/debian/pve bullseye pve-no-subscription
For ProxmoxVE 8
deb http://download.proxmox.com/debian/pve bookworm pve-no-subscription deb http://security.debian.org/debian-security bookworm-security main contrib
6. Press Ctrl + X to exit the editor, answering "Y" to the system's question about saving the file.
7. Run the command to update package lists and upgrade the system:
apt update && apt upgrade -y
8. Restart the server after the update is complete
Connecting an additional drive
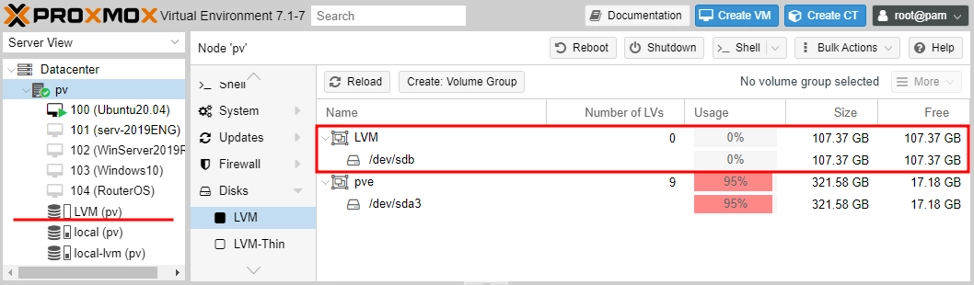
There are several options for connecting an idle drive in Proxmox. One of the fastest ways is to connect the drive as an LVM, where you can store VM and container hard disk images.
1. Check for unused drives:

One unused drive /dev/sdb is visible. It can be initialized and used as an LVM.
2. Go to the Disks/LVM section, click Create: LVM Volume Group, select the disk and name the storage

LVM partition created and can be used to host VM disk images
Take care of safety
1.Open the server console via the web interface or SSH.
2. Update package sources:
apt update
3. Install Fail2Ban:
apt install fail2ban
4. Open the utility configuration for editing:
nano /etc/fail2ban/jail.conf
5. Change the variables bantime (the number of seconds the attacker will be blocked for) and maxretry (the number of attempts to enter the login / password) for each individual service.
6. Use the Ctrl + X keyboard shortcut to exit the editor, answering "Y" to the system's question about saving the file.
7. Restart service::
systemctl restart fail2ban
You can check the status of the utility, for example, to remove blocking statistics from the blocked IP addresses, from which the attempts have been made to brute force SSH
passwords. You can do these tasks with one simple command:
fail2ban-client -v status sshd
The utility's response will look something like this:
root@hypervisor:~# fail2ban-client -v status sshd INFO Loading configs for fail2ban under /etc/fail2ban INFO Loading files: ['/etc/fail2ban/fail2ban.conf'] INFO Loading files: ['/etc/fail2ban/fail2ban.conf'] INFO Using socket file /var/run/fail2ban/fail2ban.sock Status for the jail: sshd |- Filter | |- Currently failed: 3 | |- Total failed: 4249 | `- File list: /var/log/auth.log `- Actions |- Currently banned: 0 |- Total banned: 410 `- Banned IP list:
If you encounter the error "Error is fail2ban running?", make sure that:
- The service is running:
sudo systemctl start fail2ban. - The configuration is correct:
sudo fail2ban-client -d. - The logs are readable:
sudo chmod 644 /var/log/auth.log.
In a similar way, you can close the Web interface from such attacks by creating an appropriate rule. An example of such a rule for Fail2Ban can be found in the official guide. https://pve.proxmox.com/wiki/Fail2ban










































